At Webroot we’ve been researching and chronicling developments with SpyEye since we first saw it in April 2010. This nasty Trojan is the successor to the Zeus Trojan, and it became essentially the main rootkit available for sale after the author of ZeuS left the underground market and sold ZeuS sources to the SpyEye team.
Over the last six months, through Webroot’s real-time watch technology and through my own adventures hunting malware proactively in my spare time, I’ve noticed an extreme escalation of SpyEye infections.
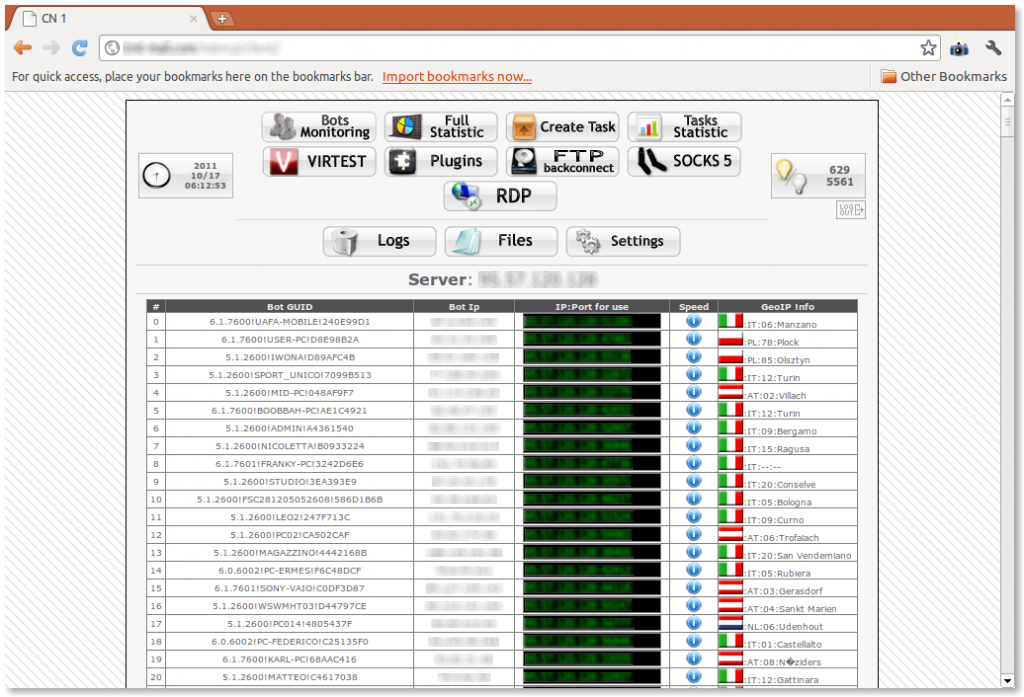
Last week I came across a URL for a password-protected site and at first didn’t think very much of it. But once I logged in, I realized I was on the administrator’s page of a SpyEye Panel, with what appeared to be full access. The administration panel was so easy to run, a fifth grader could do it.
At first glance, there were about 3,000 bots with approximately 600 active at the moment I was looking. The site was moved four days later which at that point, the number of bots was quickly approaching 10,000.
Now some of this is started to make sense. The authors of SpyEye have made it so simple to operate and in case of any trouble, apparently provide support promptly. Their selling points are working quite effectively and a lot of the wrong type of people are able to acquire the builders, Command and Control Servers for a small amount of money.
Taking a look at some of the screenshots, it doesn’t look very nice from any view.
A lot of items jumped out at me immediately. The creators have included a quick virus scan using virtest.org, since they’ve trusted the owners of the site do not share samples with any AV companies.
This allows the person running the control panel the ability to keep a constant virustotal-like scan of their binary. Once detected by enough AV companies, this person can then generate a new undetected binary.
Yet another function that grabs my attention is the use of the recent Microsoft RDP Exploit “Microsoft Security Bulletin MS11-065”
This allows the attacker the ability to establish a hidden remote desktop connection with the victim’s machine, at which time they can take screenshots or even set a recorder to run at whatever time they designate — effectively logging everything the victim does without even being logged into the control panel. The attacker can save the recordings to be viewed at his leisure.
Rest assured, the authors have gone into great detail to make the use of the SpyEye Control Panel as effective and simple to use as possible. Below is the an image of all the machines infected using the RDP Expoit.
Statistics have also been made readily available to monitor active and inactive bots by country. Notice the two cute little lightbulbs which represent online and offline bots.
Again using a nice graph layout the conroller is able is to see operating system statistics.
 |
 |
Notice the amount of infected machines by outdated operating systems as opposed to the more current Windows Operating Systems.
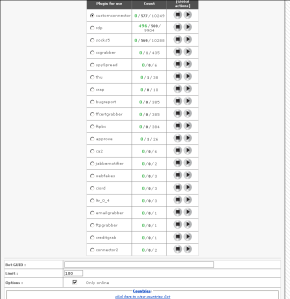
The below images show the Settings and Plugins pages. Again, more simplicity to monitor and adjust the bot’s ability.
 |
 |
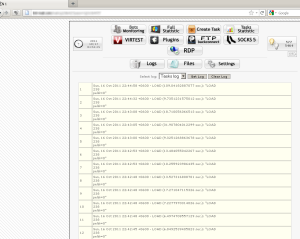
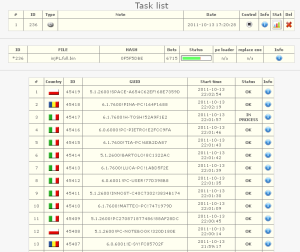
With this easily manageable admin console the “task” of creating a task is not problem at all for the controller. The below images show how the controller creates tasks such as creating a new binary or config file to deployed. These tasks are also monitored very easily, with a nice friendly layout of statistics and graphs.


Passive DNS Replication revealed a few active domains at the time I was researching this panel.
www.zolotayribka.com
teenstubegoldb.com
mapingcreating.com
tkt-mail.com
tmt-mail.com
registrationstables.com
atlanticafilms.com
www.atlanticafilms.com
The post A look inside the SpyEye Trojan admin console appeared first on Webroot Threat Blog.